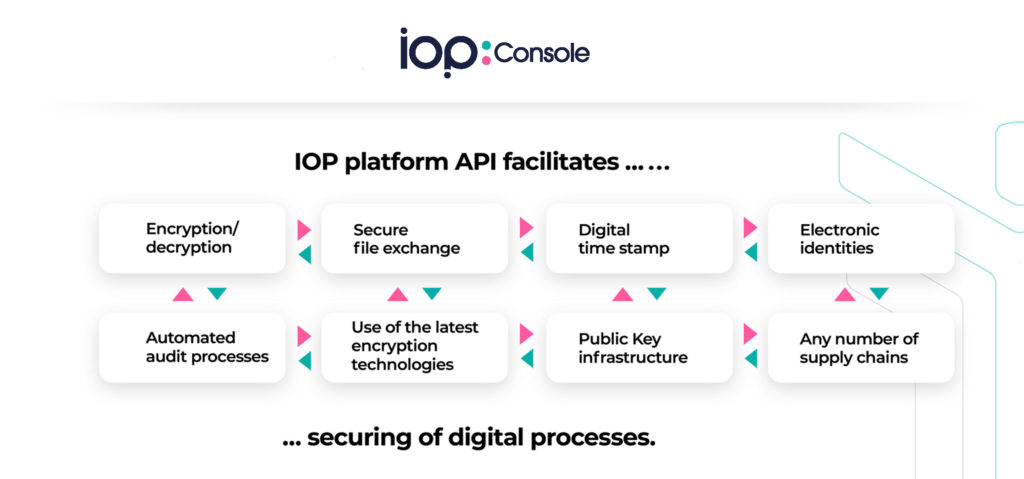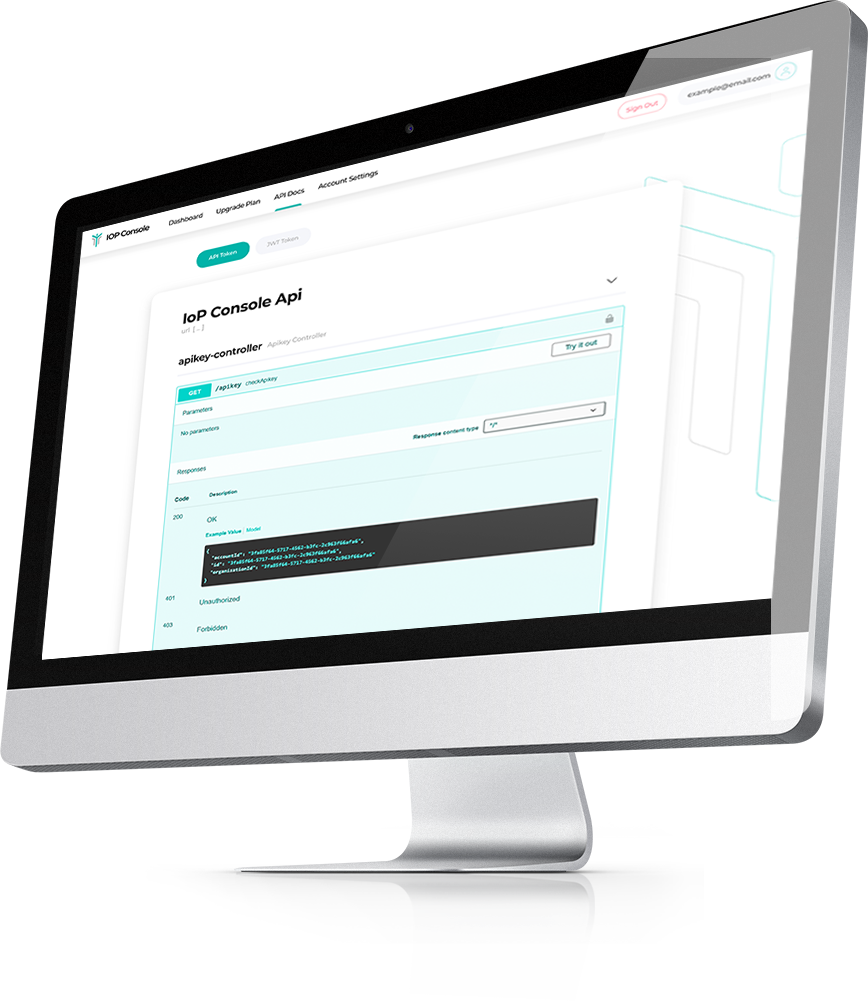
CLOUD SOLUTION FOR CONFIDENTIAL AND SECURE INTERACTIONS IN DIGITAL PROCESSES
The IOP Console is an SaaS platform for all identity management processes. With it, you can control all types of business and supply chain transactions verifiably, securely and provably. The exchange of data and information between people, companies and also machines is the important basis of all company and business processes.
With the use of SSIs (self-sovereign identities), persons, organisations as well as things receive the possibility of managing their digital identity themselves, to control it and to determine which personal attributes are to be transmitted in the course of an authentication process.
The basis is formed by DIDs (decentralized identifiers), which are created by SSI owners themselves and then – following a certification by an issuer (e.g. the postal service) – can be used referenced and as verifiable proof, so-called VCs (verified credentials).
Stored in a type of electronic wallet (ID wallet), DIDs and credentials can then be used just like ID or certificates in the analogue world to securely transmit verifiable data from one point to another.

THE ADVANTAGES ARE CLEAR
The IOP Console facilitates a reliable and tamper-proof cooperation across digital boundaries and offers companies a multitude of advantages:
- Management, control and verification of unique, verifiable, forgery-proof and addressable digital identities.
- Reliable and tamper-proof cooperation across digital boundaries.
- The user friendly web interface gives an overview of the DIDs, DNS and credentials as well as the verification of the transactions and the wallet.
- Cryptographic protection and encryption on a free and decentralized Hydra blockchain.
- 100% tamper-proof documentation of data flows, transport routes, value creation and supply chains as well as of entire business processes.
- Legally secure processes that can be verified, proven and tracked.
- Life cycle management and administration of digital company, product and personal identities.
- Secure data and document exchange in the form of signed DIDs and VCs.
- Configuration and management of access privileges and permissions.